HTTP Request action - Who can trigger link issue?
@Austen Brown and I both happened to be building adaptive cards to add to our NXT environments and could not get the card to display.
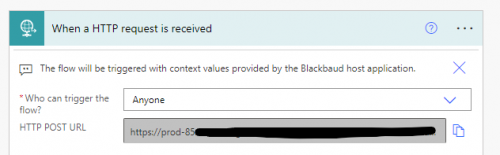
After some digging around, we noticed that the HTTP POST URL created from the HTTP action, even when encoded, was much shorter than others that were working. The only way to fix this issue was to change the “Who can trigger the flow?” from Any user in my tenant to Anyone and the link became longer and when encoded and added to the app URL all worked great?
We were both using the PA template that Blackbaud has published for creating an adaptive card so wondered if this was a bug or if the template had changed since we last used it?
@Erik Leaver @Heather McLean @Glen Hutson @Ashley Moose
Comments
-
Hey @Dan Snyder (and Austen)!
The published template pre-dates the concept of “Who can trigger the flow” that Microsoft introduced (and afaik it has not changed since it was published). Prior to that feature, the semantic was “anyone with the URL can trigger the flow”. I just tried creating a new flow using the template, and the default value is “blank” for that field so you'd need to explicitly choose an item (like “Anyone”) from the dropdown. Creating a new flow and manually specifying the HTTP Request trigger has the default value of “Any user in my tenant” (which matches the default described in the documentation).
I haven't tested the other options (Any user/specific users) but I believe they require more complex values in the request (probably involves registering an OAuth application in Azure and figuring out how to get a token, etc.).
So TLDR, I think the only way for the current implementation to work is if “Anyone” is selected.
2 -
I have created a few adaptive cards in the past month, so yes, you need to use the “anyone can invoke” option, and the security of this is in the “validate user identify token”.
2 -
Thanks for the quick responses @Ben Lambert and @Alex Wong.
1
Categories
- All Categories
- 6 Blackbaud Community Help
- High Education Program Advisory Group (HE PAG)
- BBCRM PAG Discussions
- Luminate CRM DC Users Group
- DC Luminate CRM Users Group
- Luminate PAG
- 186 bbcon®
- 1.4K Blackbaud Altru®
- 389 Blackbaud Award Management™ and Blackbaud Stewardship Management™
- 1K Blackbaud CRM™ and Blackbaud Internet Solutions™
- 14 donorCentrics®
- 355 Blackbaud eTapestry®
- 2.4K Blackbaud Financial Edge NXT®
- 616 Blackbaud Grantmaking™
- 542 Blackbaud Education Management Solutions for Higher Education
- 33 Blackbaud Impact Edge™
- 3.1K Blackbaud Education Management Solutions for K-12 Schools
- 909 Blackbaud Luminate Online® and Blackbaud TeamRaiser®
- 207 JustGiving® from Blackbaud®
- 6.2K Blackbaud Raiser's Edge NXT®
- 3.5K SKY Developer
- 236 ResearchPoint™
- 116 Blackbaud Tuition Management™
- 375 YourCause® from Blackbaud®
- 160 Organizational Best Practices
- 232 The Tap (Just for Fun)
- 31 Blackbaud Community Challenges
- Blackbaud Consultant’s Community
- 19 PowerUp Challenges
- 3 Raiser's Edge NXT PowerUp Challenge: Gift Management
- 4 Raiser's Edge NXT PowerUp Challenge: Events
- 3 Raiser's Edge NXT PowerUp Challenge: Home Page
- 4 Raiser's Edge NXT PowerUp Challenge: Standard Reports
- 4 Raiser's Edge NXT PowerUp Challenge #1 (Query)
- 71 Blackbaud Community All-Stars Discussions
- 47 Blackbaud CRM Higher Ed Product Advisory Group (HE PAG)
- 743 Community News
- 2.8K Jobs Board
- Community Help Blogs
- 52 Blackbaud SKY® Reporting Announcements
- Blackbaud Consultant’s Community
- 19 Blackbaud CRM Product Advisory Group (BBCRM PAG)
- Blackbaud Francophone Group
- Blackbaud Community™ Discussions
- Blackbaud Francophone Group








